I admit it, me too.
Actually, beyond EMP, there’s the possibility of a solar flare.
The 1859 “Carrington Event” would be far more costly if it happened now:
There was a “Cyberdeck” build posted to Reddit a while ago which included a Farraday cage w/ the idea of it being useful after such an event.
Yeah that was also the jumping off point for a time travel novel I read years ago. The basic premise was that the character traveled back to that date roughly and then ended up stuck there due to that event.
And it’s possible something like that is looming right now apparently.
Giant Sunspot Has Doubled in Size in 24 Hours and It's Pointed at Earth.
![]()
I take that back. I fear this more now. ![]()
Today’s question: what is it that a website could be trying to do that causes Windows Firewall to ask for permission? Access to less commonly used ports maybe? This is while watching some online sports stream, request comes in maybe once a day, or once per session, and only while streaming from that site.
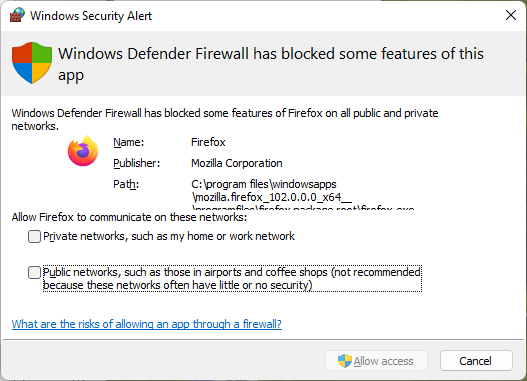
Location data would be my first suspicion. Likely harmless as many providers of live content want to know at least your rough location to make sure you aren’t streaming content that’s not authorized in your region.
Netflix does this too as I’ve seen it when I use a VPN when I’m out of the US
Thanks, but I don’t think so in this case. Whenever a site asks location data, Firefox pops up the permission request. This looks different, activating the Firewall.
except if it’s doing so by inferring from your IP address and DNS info. They do that specifically to thwart people trying to use a VPN to get around the streaming restrictions.
Oh I see, I didn’t know that sites could ask for that, and that the Firewall would be the “app” to intercept such requests.
Yeah most of the video chat apps do that too, but for a different reason which is to route you through the closest edge server which in theory anyway gives you better reliability
The reason why I’m a little suspicious that I can’t think of a single site that ever gives me this popup, so in the very least it’s “unusual”. And since streaming sites are by default “shady” (rebroadcasting is typically illegal) I’m more concerned with anything they present me with.
when it comes to that type of stuff, I’m with you.
in other words if it quacks like a duck, it’s probably a duck…
What type of duck though? ![]() I’m still thinking some kind of port scanning looking for vulnerabilities, but unfortunately I’m a security noob. Anyway, I deny access and hope for the best.
I’m still thinking some kind of port scanning looking for vulnerabilities, but unfortunately I’m a security noob. Anyway, I deny access and hope for the best.
Edit: looks like trying to access an uncommon port is a likely scenario. from Microsoft (emphasis mine)
There are two ways to allow an app through Windows Defender Firewall. Both of them are risky:
Add an app to the list of allowed apps (less risky).
Open a port (more risky).
When you open a port in Windows Defender Firewall you allow traffic into or out of your device, as though you drilled a hole in the firewall. This makes your device less secure and might create opportunities for hackers or malware to use one of those openings to get to your files or use your device to spread malware to other devices.
Generally, it’s safer to add an app to the list of allowed apps than to open a port. A port stays open until you close it, but an allowed app opens the “hole” only when needed.
To help reduce your security risk:
Only allow an app or open a port when you really need to, and follow the steps to remove apps from the list of allowed apps or close ports that you no longer need.
Never allow an app that you don’t recognize to communicate through the firewall.
That’s likely exactly the tool(s) being employed. Again if something like Facebook is doing it, it’s harmless (other than of course it’s Facebook) , But like you said if you think there is anything even remotely dodgy about a site, it probably is and it’s wisest to be extra cautious .
BTW: Xbox live uses port scanning technology too. But they do it for good reason to prevent you from mucking with things and the xbox app on windows suppresses the alert otherwise
We copy and paste that to customers all of the time ![]()
Looking at the Event Viewer for Microsoft-Windows-Windows Firewall With Advanced Security/Firewall I see that it was an UDP request. Seems like it could be innocuous, it’s a less secure (?) way to stream data packets allowing for packet loss and out of order arrival. Still not sure if it could also open me up to exploits.
Rule ID: UDP Query User{TPCR-1234-5678-JOES-SECURITEASE}C:\program files\windowsapps\mozilla.firefox_102.0.0.0_x64\vfs\programfiles\firefox package root\firefox.exe
Rule Name: Firefox
Origin: Local
Active: Yes
Direction: Inbound
Profiles: Public
Action: Block
Application Path: C:\program files\windowsapps\mozilla.firefox_102.0.0.0_x64\vfs\programfiles\firefox package root\firefox.exe
Service Name:
Protocol: UDP
Security Options: None
Edge Traversal: None
Modifying User: NT SERVICE\mpssvc
Modifying Application: C:\WINDOWS\System32\svchost.exe
In today’s security freakout, I just had a hard crash on my SLS (went from typing to staring at the boot logo in a tenth of a second), and looked through recently changed files and recent errors in the event viewer (always a bad idea…).
[edit half a year later: probably a combination of a hardware issue and my own paranoia. I ended up doing a full wipe and reinstall, and a lot of the same errors show up. The hard crash happened twice, but hasn’t returned since I swapped the Hynix SSD for a Samsung SSD]
I see some modified files right after the crash in the C:\windows\panther folder, which is a legitimate folder, but it’s pretty rare to see anything about it on the internet. Of the 12 google hits for “c:\windows\panther” from the past year, one of them is on https://segmentfault.com/a/1190000040565520/en mentioning “Unattend.xml sysprep.xml and sysprep.inf file GPP.xml has certain information leakage, they usually exist in the following path: C:\Windows\Panther” and “Once found, find the tags in the Unattend.xml file. It is possible to find the user’s encrypted password.”
I also like this line from Event Viewer: “The AllowInsecureGuestAuth registry value is not configured with default settings.” and the friendly explanation "This event indicates that an administrator has enabled insecure guest logons. " Probably innocuous, but sure looks dubious! Right after that I see this warning: and One or more named pipes or shares have been marked for access by anonymous users. This increases the security risk of the computer by allowing unauthenticated users to connect to this server.
Right after that a warning “Open Key operation failed. Cryptographic Parameters: Provider Name: Microsoft Software Key Storage Provider, Key Name: (long list of numbers)”
After that I see that Defender attempted to load something that didn’t meet Antimalware signing level requirements: “Code Integrity determined that a process (\Device\HarddiskVolume3\ProgramData\Microsoft\Windows Defender\Platform\4.18.2205.7-0\MsMpEng.exe) attempted to load \Device\HarddiskVolume3\Windows\System32\DriverStore\FileRepository\iigd_dch.inf_amd64_d3a7501d49d450c8\igd10iumd64.dll that did not meet the Custom 3 / Antimalware signing level requirements.”
I also see a “MCU Critical Error” for SurfaceService, that one only has two google hits.
So now the question is… nothingburger or real problem? Do I take any action? I changed the main password on my Outlook account that I also use to log on to my PC, not sure what else I could do. Restore from a recent “restore point”? I have one from two days ago. Or just blissfully pretend/assume that nothing happened?
So it’s a good news bad news scenario from what I can gather. It looks like Defender actually did it’s job against an attempted intrusion, albeit less than elegantly.
I noticed there were a significant number of definition updates in this past Tuesdays patch Tuesday update and if you hadn’t updated and/or were partially updated, it could have caused what you experienced .
Hard to say for sure without a more forensic look, but I do suspect one or more of the sites you have been looking have may be compromised. Your’s looks almost identical to a hack that XDA had for a few days early last year, and which one of our developers got caught by.
Thanks. And also… Help! ![]() So the bad news is that I only had my usual sites open in Firefox, so if this really is a hack (attempt), it came from a place I visit daily. So that bodes well…
So the bad news is that I only had my usual sites open in Firefox, so if this really is a hack (attempt), it came from a place I visit daily. So that bodes well…
Which aspects of what I mention look similar to the XDA hack? And any steps you recommend? Nuke everything and install Win11 from scratch? Run something other than Defender to look for remaining threats?